Domain-based Message Authentication, Reporting, and Conformance
Email Administrators Guide: Unmasking DMARC and Defeating Scammers
Table of Contents
Email security has become a paramount concern for organizations in today’s digital landscape. As email administrators, it is essential to stay ahead of the curve and implement robust measures to protect the integrity of communication channels. One such powerful security protocol that can significantly enhance email security is DMARC (Domain-based Message Authentication, Reporting, and Conformance). In this article, we will delve into the world of DMARC, its components, implementation, and the benefits it offers in safeguarding organizations against email fraud, phishing, and spoofing attacks.
Understanding DMARC
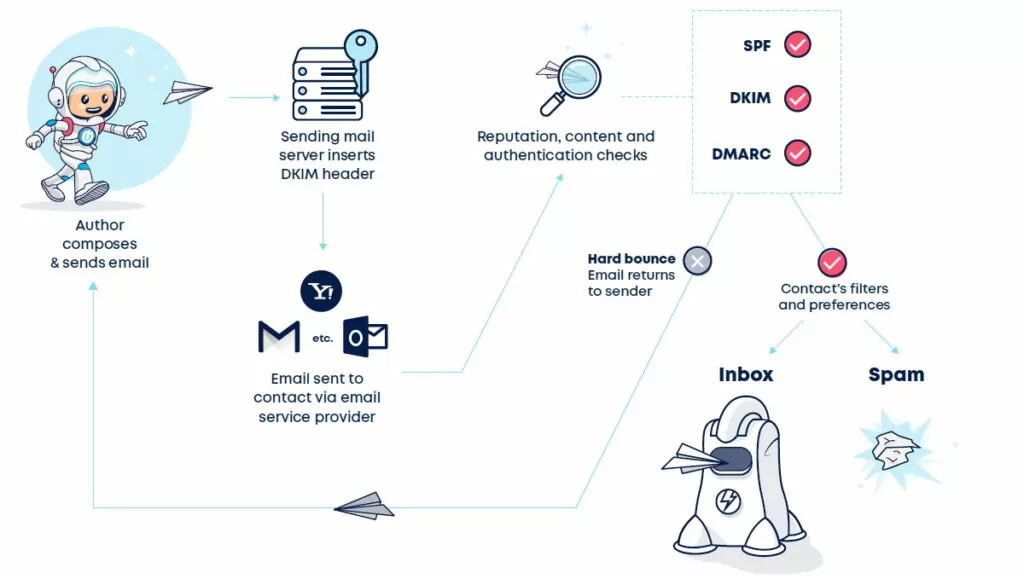
DMARC, an acronym for Domain-based Message Authentication, Reporting, and Conformance, is a security protocol that builds upon existing email authentication mechanisms such as SPF (Sender Policy Framework) and DKIM (DomainKeys Identified Mail). Its primary objective is to prevent unauthorized entities from exploiting the trust associated with a particular domain, thus mitigating email forgery, phishing attempts, and domain spoofing.
By deploying DMARC, email administrators add an extra layer of protection to their organization’s email deliverability. DMARC facilitates sender authentication by allowing domain owners to publish policies that specify how receiving mail servers should handle messages from their domains.
Unmasking DMARC: Defeat Scammers. Subscribe to Our Newsletter!
Stay informed with our exclusive tips and updates on email security. Subscribe now!
Key Components of DMARC
DMARC policies dictate the actions that receiving mail servers should take with emails that fail authentication. There are four possible policy options:
- P (None): Receiving mail servers collect and provide DMARC reports but take no action based on the results. This policy is useful for monitoring and gathering data without affecting email delivery.
- P (Quarantine): Emails failing DMARC authentication are treated as suspicious. Receiving servers can choose to deliver them to the recipient’s spam/junk folder. Deploying this policy aids in identifying potential threats.
- P (Reject): Emails that fail DMARC authentication are rejected and not delivered to the recipient’s inbox. This policy provides the highest level of protection against fraudulent emails but requires careful consideration to avoid affecting legitimate senders inadvertently.
Aligning SPF and DKIM Authentication
DMARC relies on the alignment of SPF and DKIM, two existing email authentication mechanisms, with the “From” domain to validate sender legitimacy.
Sender Policy Framework (SPF): This mechanism adds information to the DNS (Domain Name System) records of the sending domain, detailing the authorized IP addresses or hosts that are allowed to send emails on behalf of the domain. To align SPF with DMARC, organizations need to ensure that their SPF records correctly list all authorized sending sources for their domain.
DomainKeys Identified Mail (DKIM): DKIM utilizes public and private key cryptography to sign outgoing emails, ensuring the integrity of messages and validating the identity of the sender. For successful DMARC deployment, organizations should enable DKIM signing and ensure DKIM signatures match the “From” domain.
Utilizing DMARC Reports
DMARC generates two types of reports: aggregate and forensic.
Aggregate Reports: These reports provide high-level information on email authentication results received from various sources. Analyzing aggregate reports enables administrators to gain insights into the email authentication landscape, track overall email deliverability rates, and identify potential threats or misconfigurations.
Forensic Reports: Forensic reports provide detailed data about specific email authentication failures. These reports help administrators investigate and diagnose potential incidents, allowing them to take appropriate actions to mitigate security risks.
Implementing DMARC
Implementing DMARC requires a systematic approach to ensure a smooth transition and effective deployment. Here’s a step-by-step guide for email administrators:
- Assess the current email ecosystem and document all legitimate email sources, including internal and third-party services.
- Analyze SPF and DKIM implementation across legitimate sources. Ensure all sending sources align with the relevant email authentication standards.
- Introduce a “none” policy initially to generate aggregate reports without impacting email delivery.
- Analyze the generated reports to identify and address any authentication failures or policy violations. Make necessary adjustments to ensure compliance.
- Gradually switch the DMARC policy to “quarantine” or “reject” after thorough analysis and implementation of corrective actions.
- Monitor DMARC reports regularly to stay up-to-date with email authentication status and address any emerging issues or anomalies.
It’s worth noting that the implementation process may encounter challenges, such as misconfigured third-party systems, unauthorized senders, or complex email infrastructures. Consulting with industry experts or seeking assistance from vendors with significant DMARC expertise can be beneficial to overcome such hurdles effectively.
Analyzing DMARC Reports
Aggregate Reports:
- Analyze authentication results to identify domains experiencing high failure rates, potential spoofing attempts, or misconfigurations.
- Identify sending sources that consistently fail authentication to root out potential unauthorized senders or misconfigured legitimate sources.
- Track overall email authentication trends over time and evaluate the impact of policy changes or infrastructure updates.
Forensic Reports:
- Review individual failure reports to investigate the root causes behind specific failures, such as DKIM signature failures or SPF alignment issues.
- Address authentication failures promptly by taking appropriate corrective measures, such as updating SPF records or reconfiguring DKIM settings.
- Make use of forensic reports to identify patterns and potential threats. Prompt action against suspicious activity can prevent email-based security incidents.
Industry Adoption and Future Trends
Over the years, the adoption of DMARC has steadily increased. Organizations are recognizing its effectiveness in combating email fraud and improving deliverability. However, implementation rates may still vary across industries.

As cyber threats continue to evolve, the future of DMARC lies in its continued development and wider adoption. Enhancements and emerging trends may include stricter policies, improved reporting mechanisms, and increased collaboration among organizations to share threat intelligence effectively.
Unmasking DMARC: Defeat Scammers. Subscribe to Our Newsletter!
Stay informed with our exclusive tips and updates on email security. Subscribe now!
In Conclusion
DMARC serves as a powerful tool for email administrators to enhance the security of their organization’s email landscape. By implementing DMARC policies and aligning SPF and DKIM authentication, organizations can effectively reduce the risk of email fraud, phishing, and domain spoofing. Continuous monitoring and analysis of DMARC reports allow administrators to detect, diagnose, and address potential vulnerabilities, fostering a secure environment for communication. As email administrators, embracing DMARC is crucial to safeguarding both your organization’s reputation and the trust of your recipients.
