ARC -Authenticated Received Chain
Mastering Authentication: The ABCs of Implementing ARC for Email
Unlock the secrets of authentication! Discover the power of implementing ARC for email and conquer the authentication game today.
Table of Contents
As businesses continue to rely heavily on email communication, security and authenticity become paramount. In order to combat email spoofing and phishing attempts, organizations are adopting various email authentication protocols. One such protocol, Automatic Rate Control (ARC), offers a promising solution. This blog post aims to provide a neutral and comprehensive guide on implementing ARC for streamlined email management.
Understanding the Basics of ARC
ARC, short for Automatic Rate Control, is an email authentication framework designed to improve trust and security. Its primary purpose is to verify the authenticity and integrity of emails, ensuring they have not been tampered with during transmission. By utilizing cryptographic signatures, ARC helps prevent email spoofing and protects against malicious activities.
The framework operates through a set of interconnected components and stakeholders. Senders, receivers, and intermediate handlers collaborate to validate the email’s journey, ensuring that it comes from a genuine source and that its content remains unchanged throughout the transmission process.
ARC plays a crucial role in enhancing email authentication and security by seamlessly integrating with other widely adopted protocols such as SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance). Together, these protocols provide a layered defense against email fraud, safeguarding organizations and individuals from phishing attacks and other email-based threats.
Level up your email security: Master ARC authentication now!
Stay in the loop! Subscribe to our newsletter for the latest authentication insights.
Preparing for ARC Implementation
Before diving into ARC implementation, it is crucial to conduct an audit of your existing email infrastructure. This audit will help identify the areas that may require adjustment or further attention to ensure a smooth integration process.
Furthermore, verifying the compatibility of stakeholders involved is crucial. It is essential to confirm if email senders and receivers support ARC. Collaboration with your email service providers and other trusted parties can help assess the feasibility of adopting ARC within your organization.
Additionally, since ARC complements existing email authentication measures, ensuring compatibility with these protocols is essential. DNS records need to be properly configured to allow ARC to function alongside SPF, DKIM, and DMARC protocols.
Image courtesy of via Google Images
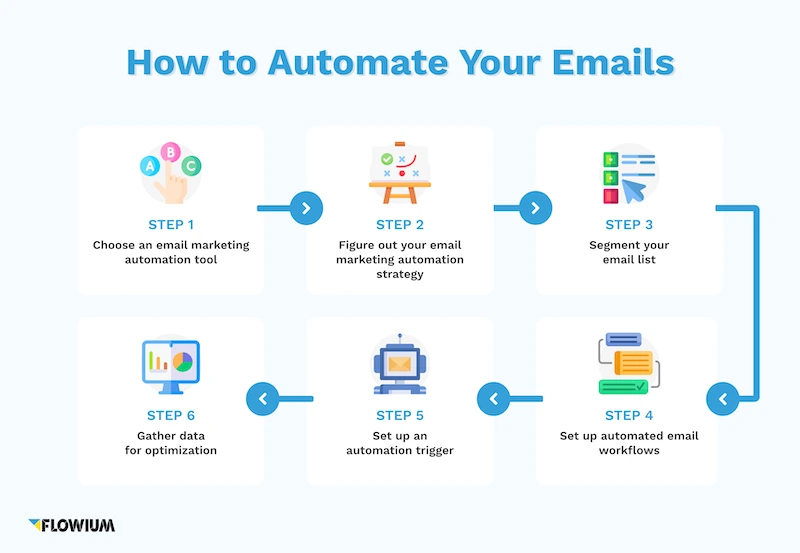
1. Planning and Goal-Setting for ARC Implementation: Start by establishing clear objectives for implementing ARC within your organization. Define the desired outcomes and the metrics you’ll use to measure success. This will help guide your implementation strategy.
2. Configuring DNS Records for ARC: Modify your domain’s DNS records to include ARC-related information. These records enable email senders and receivers to authenticate and validate the email’s journey based on the ARC framework.
3. Collaborating with Email Providers and Authentication Systems: Engage with your email service providers and any third-party authentication systems you rely on. Ensure their systems are compatible with ARC and discuss any necessary adjustments or configurations that may be needed.
4. Testing and Verifying ARC Functionality: Thoroughly test the ARC implementation to verify its effectiveness. Send and receive emails, monitoring their journey and verifying that the ARC-related information is correctly handled and interpreted by all stakeholders involved. Address any issues encountered during the testing phase promptly.
Step-by-Step Guide to Implementing ARC
Successful ARC implementation requires a systematic approach. Consider the following steps to ensure a smooth integration process:
Addressing Common Challenges and Limitations
While ARC brings a range of benefits, organizations need to be aware of potential challenges and limitations they may face during implementation:
1. Dealing with Legacy Systems and Older Email Clients: ARC may not be fully supported by some older email clients or legacy systems. It’s crucial to assess the compatibility of all stakeholders and make appropriate accommodations while transitioning to ARC.
2. Addressing Potential Performance and Deliverability Impacts: Introducing new protocols can sometimes impact email performance and deliverability. Monitor your email deliverability metrics closely during and after the ARC implementation, making adjustments as necessary.
3. Handling Non-Compliant Email Senders and Receivers: Not all email senders and receivers may have embraced ARC. Establish a clear communication strategy to address non-compliance issues, ensuring your organization can consistently benefit from ARC’s protective measures.
Best Practices for ARC Management and Maintenance
To maximize the effectiveness of ARC and maintain its benefits over time, consider implementing the following best practices:
Image courtesy of via Google Images
1. Developing a Robust Email Policy Framework: Create comprehensive email policies that include guidelines on implementing and maintaining ARC. These policies will help ensure consistent adherence to ARC standards and practices across your organization.
2. Regularly Monitoring ARC-related Logs and Reports: Keep an eye on ARC-related logs and reports, as they may contain valuable information about authentication failures or potential malicious activities. Regular monitoring will allow you to promptly address any issues that arise and maintain a secure email environment.
3. Keeping Up-to-Date with Industry Developments: Stay informed about evolving email authentication standards and industry advancements. Being aware of updates and changes will help your organization adapt to new technologies or requirements, allowing you to continuously enhance your email security measures.
Evaluating the Success of ARC Implementation
Once ARC has been successfully implemented, it’s crucial to evaluate its impact and effectiveness. Consider the following steps:
1. Establishing Key Performance Indicators (KPIs): Develop clear KPIs to measure the success of your ARC implementation. These may include metrics such as reduced phishing attempts, improved email deliverability rates, or enhanced brand reputation.
2. Measuring the Impact on Email Deliverability and Security: Analyze email deliverability rates and security metrics before and after the ARC implementation. Compare the results to determine the overall improvements or changes brought about by ARC’s adoption.
3. Gathering Feedback from Email Senders and Recipients: Engage with both internal and external stakeholders to collect feedback on their experience with ARC-enabled emails. Their perspectives can provide valuable insights on any potential issues or improvements that might be necessary.
Conclusion
Implementing ARC for streamlined email management presents significant advantages in terms of email authenticity and security. By adhering to the outlined steps and best practices, organizations can harness the power of ARC to combat fraudulent email activities successfully. Embrace ARC today as an essential layer of defense for your email infrastructure, ensuring the trust and security of your communications.
